Hyper-V network adapters: create, configure and remove
Here you will find out:
- what Hyper-V is
- how you can set up Hyper-V network adapters
- when DiskInternals can help you
Are you ready? Let's read!
How to construct a Hyper-V virtual machine was discussed in the previous blog article (VM). Creating a Hyper-V VM, on the other hand, is only the first step in creating a large-scale virtual environment; you must also verify that VMs running on a Hyper-V host can interact with one another. You'll need to know about Hyper-V network adapters, the technology underlying Hyper-V networking, and how to configure Hyper-V networking for this.
Hyper-V Networking
A virtual network adapter (sometimes referred to as a virtual NIC) is a virtualized version of a real network adapter. It connects a physical server to other servers, virtual machines, or other networking devices across a LAN connection in Hyper-V settings. In a nutshell, vNIC is responsible for enabling and managing all network communications.
Each VM contains one or more virtual network interface cards (vNICs), which connect to a single subnet. However, you may give that NIC various IP addresses to obtain access to multiple subnets.
When you install the Hyper-V role on your computer and start generating new VMs, you should be aware of the default networking configurations.
- 1. Virtual switches were not available in earlier Windows versions (before to Windows 10). When Hyper-V is enabled on Windows 10, however, you may utilize a Default Switch for smooth networking since it gives you access to the host's network.
- 2. Virtual network adapters in Hyper-V allow VMs to communicate with each other via a virtual switch. Newly generated VMs, on the other hand, have no virtual switches attached to them. Each new VM comes with a network adapter that you may configure by assigning a single virtual switch or leave unplugged. As a result, you must establish a virtual switch and configure a virtual network adapter to allow network connectivity.
Different levels of network access are provided by three virtual switches:
- A physical network adapter can be connected to an external virtual switch, allowing VMs to access the physical network. An external virtual switch allows VMs on the same physical machine, as well as VMs and the physical computer, to communicate and access the physical network.
- An internal virtual switch allows communication between VMs running on the same Hyper-V server, as well as between the management OS and those VMs. This form of switch, however, does not provide access to a physical network.
- Only the VMs that operate on the same Hyper-V host are connected via a private virtual switch. This form of network allows for network communication that is separated.
VLAN tagging, which is a way of giving a particular tag (VLAN ID) to each packet running on the network, is also worth mentioning. VLAN tagging makes it easier to figure out which information packets belong to which VLAN. As a consequence, this strategy allows you to isolate network traffic while still ensuring that network communications are uninterrupted.
There are two types of virtual network adapters in Hyper-V:
- Only Generation 1 VMs may use legacy network adapters, which simulate a real network adapter. For unenlightened guest VMs that don't support Hyper-V Integration Services or Linux Integration Services, this network adapter is utilized. On a single VM, up to four old vNiCs can be installed. Furthermore, a legacy network adapter is used to allow communication between guest OSes that are not Hyper-V compatible.
- The guest OSes can be installed over the network using legacy vNiCs. Enlightened guest VMs that use Hyper-V Integration Services or Linux Integration Services employ synthetic network adapters. On a single VM, up to 8 synthetic vNICs can be deployed. They usually outperform legacy vNICs in terms of performance. VMBus, which allows and manages communication between distinct partitions, enables network connectivity in this situation. Furthermore, you may utilize VLAN tagging with this sort of network adapter.
Configure Virtual Network Adapter
You may enable and configure a Hyper-V network adapter in one of two ways: using the graphical user interface (GUI) in Hyper-V Manager or through PowerShell scripts. We'll go through both of them in depth. Now, let's have a look at the first method:
1. Go to Hyper-V Manager and open it.
2. Right-click the VM name for which you want to install a Hyper-V network adapter and choose Add Hyper-V Network Adapter. Make a selection of options.
3. A new menu will appear, displaying information about the virtual machine's settings. Select Add Hardware from the Hardware Section to view a list of devices you may add to your VM. In our scenario, there are just two possibilities: Network Adapter and Legacy Network Adapter (which is only available for Generation 1) are two different types of network adapters.
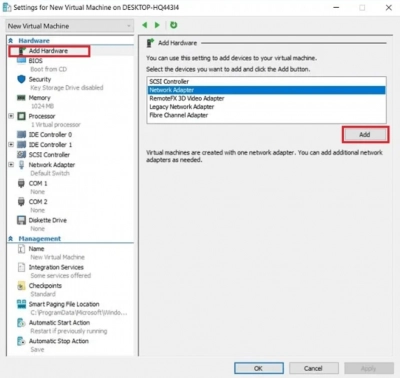
4. You'll be led to the Network Adapter area, where you may setup a new Hyper-V network adapter by connecting to a virtual switch, enabling VLAN identification and defining VLAN ID, and setting the maximum and minimum bandwidth utilization. By choosing Remove, you may also get rid of the Hyper-V network adapter.
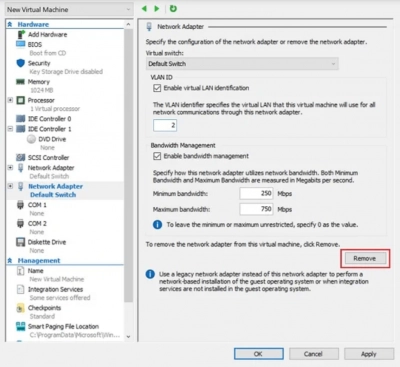
5. To preserve your changes, click Apply.
You may also change the hardware acceleration settings and activate more sophisticated capabilities in Hyper-V Manager.
1. In the Hardware section, double-click Network Adapter. Select Hardware Acceleration from the drop-down menu. You can activate VMQ and IPsec task offloading, as well as set the maximum number of Offloaded SAs, in this section (security associations). The Hyper-V Virtual Machine Queue is a hardware virtualization mechanism that guarantees immediate network data delivery to the shared memory of the virtual machine. IPsec is a security protocol that encrypts network data transmissions. You can transfer IPsec-related operations to a network adapter with IPsec task offloading enabled to avoid overusing hardware resources.
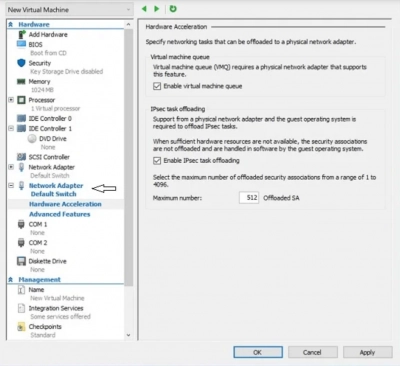
2. To preserve your changes, click Apply.
3. Next, pick Advanced Capabilities to configure the virtual network adapter's advanced features. MAC address, DHCP guard, Router guard, Protected network, Port mirroring, and NIC teaming are just a few of them. Each feature is accompanied by a brief explanation on how to utilize it. Take a look at them and pick which features you want to enable.
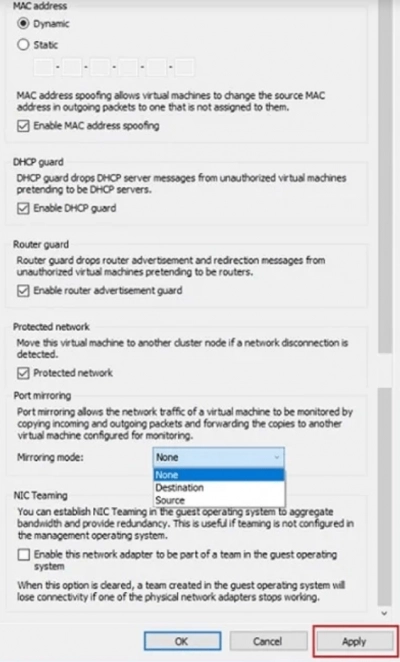
4. To save your changes, check the relevant boxes and click Apply.
Use PowerShell to Manage Hyper-V Network Adapters
As can be seen, Hyper-V Manager's setup choices are relatively restricted. Furthermore, you can only set up Hyper-V network adapters for guest VMs using the GUI, not for the management OS. As a result, PowerShell may be utilized to provide more complex functionality as well as a variety of configuration choices. Let's have a look at how PowerShell can handle Hyper-V network devices.
Hyper-V network adapters creation
You must execute PowerShell in administrator mode in order for the PowerShell cmdlets to operate. To do so, put PowerShell into a search box, right-click the PowerShell icon, and choose Run as Administrator from the context menu.
To add a new virtual network adapter to a Hyper-V VM, use the Add-VMNetworkAdapter cmdlet. An example of how to use this cmdlet is shown below:
Add-VMNetworkAdapter -VMName DemoVM -SwitchName DemoVSwitch –Name ‘Demo Network Adapter’
In the management OS, the following example shows how to create a second virtual network adapter:
Add-VMNetworkAdapter -ManagementOS -Name ‘Second Network Adapter’
Connect or disconnect adapters
Connecting a virtual network adapter to a virtual switch of your choosing is possible using the Connect-VMNetworkAdapter cmdlet. The example below shows how to simultaneously install one virtual switch (Default switch) to two virtual machines (DemoVM and New Virtual Machine). Make sure none of the virtual machines is operating.
Connect-VMNetworkAdapter -VMName DemoVM, ‘New Virtual Machine’ -SwitchName ‘Default Switch’
The Detach-VMNetworkAdapter cmdlet may be used to disconnect a Hyper-V network adapter from a virtual switch or an Ethernet resource pool. You may disconnect all network adapters from a single VM named DemoVM using the script below:
Disconnect-VMNetworkAdapter -VMName DemoVM
This PowerShell script can be used to disconnect all virtual network adapters that are connected to a virtual switch Default Switch in all VMs in Hyper-V environment.
Get-VMNetworkAdapter -VMName *| Where-Object {$_.SwitchName -eq 'Default Switch'} | Disconnect-VMNetworkAdapter
With PowerShell, you can be even more precise in your configurations. If you want to disconnect all network adapters that are connected to a particular virtual switch (Default Switch) that are running on a certain VM (DemoVM), use the cmdlet below:
Get-VMNetworkAdapter -VMName DemoVM | Where-Object {$_.SwitchName -eq 'Default Switch'} | Disconnect-VMNetworkAdapter
Remove adapters
This cmdlet is used to delete one or more virtual network adapters from a virtual machine (VM) as well as the management OS.
The network adapter NewNetworkAdapter is deleted from a VM named DemoVM in the following example:
Remove-VMNetworkAdapter -VMName DemoVM -VMNetworkAdapterName NewNetworkAdapter
The following example demonstrates how to disable the network adapter Secondary in the administration OS:
Remove-VMNetworkAdapter -ManagementOs -Name Secondary
Rename adapters
On the management OS, you may also rename a Hyper-V network adapter of a specific VM:
Rename-VMNetworkAdapter -VMName DemoVM -NewName ‘Network Adapter 2019’
You may check that all network adapters of a VM named DemoVM have been correctly renamed in Hyper-V Manager.
Run the following script to rename a network adapter (Network Adapter 2019) of a specific VM (DemoVM):
VMNetworkAdapter -VMName Demo rename VM -NewName 'Hyper-V network adapter' -Name 'Network Adapter 2019'
The following cmdlet may be used to rename a management OS network adapter.
Rename-VMNetworkAdapter -ManagementOs -Name Adapter -NewName ‘Communications Channel’
Set adapters
This section contains a set of cmdlets that may be used to configure the Hyper-V network adapter's functionality in a Hyper-V VM or the management OS. It might take a long time to go over all of the setup choices in detail. As a result, we'll simply go through a handful of the PowerShell capabilities that may be activated.
You may enable DHCP Guard, for example, by running the script below. DHCP Guard is a system security feature that protects the system from illegal access from the guest OS.
Set-VMNetworkAdapter -VMName DemoVM -DhcpGuard On
You may also activate Port Mirroring, which allows you to copy and transfer network packets from one virtual network adapter to another. Source and Destination are the two mirroring modes. We agree that the network traffic of this specific network adapter will be duplicated and delivered to the monitoring VM by selecting Source mode. A Destination mirroring mode will be assigned to that VM's network adapter. In order for this functionality to function, each Source network adapter must be allocated a Destination network adapter.
Run the following script to activate Port Mirroring in Source mode:
Set-VMNetworkAdapter -VMName DemoVM –Name ‘Hyper-V network adapter’-PortMirroring Source
This cmdlet will activate the Port Mirroring capability on the DemoVM VM and attach its virtual network adapter to the source role.
The Monitoring virtual network adapter is configured as the port mirroring destination point in the following example. As a consequence, a VM named DemoVM ('Source') will monitor the VM named 'New Virtual Machine's' network traffic (Destination).
Set-VMNetworkAdapter -VMName ‘New Virtual Machine’-Name Monitoring -PortMirroring Destination
To enable VLAN identification as well as assign a specific VLAN ID, use the following cmdlet:
Set-VMNetworkAdapterVlan -VMName DemoVM -VMNetworkAdapterName ‘Hyper-V network adapter’ -Access -VlanId 20
VLAN tagging will be enabled on a specific Hyper-V network adapter (Hyper-V network adapter) that is attached to a specific VM in this situation (DemoVM).
Alternatively, run the following cmdlet to deactivate VLAN tagging:
Set-VMNetworkAdapterVlan -VMName DemoVM -VMNetworkAdapterName ‘Hyper-V network adapter’ -Untagged
The biggest benefit of using PowerShell cmdlets is that you may arrange them as you want and construct complex scripts. You may significantly speed up the process of managing and configuring your Hyper-V setup with their assistance.
Get network adapters
These PowerShell scripts can be used to access information about the virtual network adapters that are present on a particular VM, on the management OS, or on all VMs as well as the management OS running in the virtual environment. All of the cmdlets are presented below:
For a single VM:
Get-VMNetworkAdapter –VMName DemoVM
For the management OS:
Get-VMNetworkAdapter -ManagementOS
For all VMs in Hyper-V environment, including the management OS:
Get-VMNetworkAdapter -All
If the final script is properly implemented, you will see the following screen containing information about your Hyper-V network adapters:
Remove Hyper-V network adapters
This cmdlet is used to remove one or more virtual network adapters from a VM, as well as from the management OS.
In the next example, the network adapter NewNetworkAdapter is removed from a VM named DemoVM:
Remove-VMNetworkAdapter -VMName DemoVM -VMNetworkAdapterName NewNetworkAdapter
The example below shows how you can remove the network adapter Secondary from the management OS:
Remove-VMNetworkAdapter -ManagementOs -Name Secondary
Rename Hyper-V network adapters
You can also rename a Hyper-V network adapter of a particular VM or on the management OS:
Rename-VMNetworkAdapter -VMName DemoVM -NewName ‘Network Adapter 2019’
In Hyper-V Manager you can verify that all network adapters of a VM named DemoVM have been successfully renamed.
To give a new name to a network adapter (Network Adapter 2019) of a particular VM (DemoVM), run the following script:
Rename-VMNetworkAdapter -VMName DemoVM -Name ‘Network Adapter 2019’ -NewName ‘Hyper-V network adapter’
The next cmdlet can help you to rename a network adapter of the management OS.
Rename-VMNetworkAdapter -ManagementOs -Name Adapter -NewName ‘Communications Channel’
Set Hyper-V network adapters
This section contains a set of cmdlets that may be used to configure the Hyper-V network adapter's functionality in a Hyper-V VM or the management OS. It might take a long time to go over all of the setup choices in detail. As a result, we'll simply go through a handful of the PowerShell capabilities that may be activated.
You may enable DHCP Guard, for example, by running the script below. DHCP Guard is a system security feature that protects the system from illegal access from the guest OS.
Set-VMNetworkAdapter -VMName DemoVM -DhcpGuard On
You may also activate Port Mirroring, which allows you to copy and transfer network packets from one virtual network adapter to another. Source and Destination are the two mirroring modes. We agree that the network traffic of this specific network adapter will be duplicated and delivered to the monitoring VM by choosing Source mode. A Destination mirroring mode will be assigned to that VM's network adapter. In order for this functionality to work, each Source network adapter must be allocated a Destination network adapter.
Run the following script to activate Port Mirroring in Source mode:
Set-VMNetworkAdapter -VMName DemoVM –Name ‘Hyper-V network adapter’-PortMirroring Source
This cmdlet will activate the Port Mirroring capability on the DemoVM VM and attach its virtual network adapter to the source role.
The Monitoring virtual network adapter is configured as the port mirroring destination point in the following example. As a consequence, a VM named DemoVM ('Source') will monitor the VM named 'New Virtual Machine's' network traffic (Destination).
Set-VMNetworkAdapter -VMName ‘New Virtual Machine’-Name Monitoring -PortMirroring Destination
The following cmdlet can be used to enable VLAN identification as well as to assign a specific VLAN ID:
Set-VMNetworkAdapterVlan -VMName DemoVM -VMNetworkAdapterName ‘Hyper-V network adapter’ -Access -VlanId 20
In this case, VLAN tagging will be enabled on a particular Hyper-V network adapter (Hyper-V network adapter) that is connected to a certain VM (DemoVM).
Or, if you want to disable VLAN tagging, type this cmdlet:
Set-VMNetworkAdapterVlan -VMName DemoVM -VMNetworkAdapterName ‘Hyper-V network adapter’ -Untagged
The main advantage of the PowerShell cmdlets is that you can arrange them in any way you want, and create comprehensive scripts. With their help, you can considerably optimize the process of managing and configuring your Hyper-V environment.
Recover Lost Data Using DiskInternals RAID Recovery
DiskInternals RAID Recovery is a professional software application that allows you to recover lost files and partitions from all kinds of RAID arrays. It is the favorite RAID backup & recovery tool of many IT experts; this software program has been regularly updated for more than 15 years.
Tip: Discover the difference between Hyper-V and VMware recovery!More interestingly, DiskInternals RAID Recovery comes with a suite of useful features, as well as support various file systems. With the software, you would definitely get back your lost data from both software and hardware RAIDs; it works for macOS, Linux, and Windows OS. There are three (3) recovery modes supported by this program; there is also a built-in Recovery Wizard to guide users.
This VHD recovery tool is reliable and works only on Windows PCs. It supports all file types and works pretty very fast.
First Step:
Firstly, you need to turn off your computer/network server and disconnect the RAID drives in the array.
Second Step:
Remove the drives and connect them to a computer system via USB or any other supported means of connectivity.
Third Step:
Boot the computer where the hard drives are connected and install DiskInternals RAID Recovery software. After the installation, launch the program and follow the Recovery Wizard prompts to recover your lost files from each of the connected drives, one after another.
Recovery Tips
These are tips you should have at the back of your mind when attempting to recover files using DiskInternals RAID Recovery.
- Don’t rush the process - allow each step to run completely and successfully before proceeding to the next. Else, you may not recover all your lost files.
- Verify that you chose the exact disk drive that had the lost files you want to recover. If you select the wrong drive, you won’t get back any of the lost files.
- DiskInternals RAID Recovery comes with a previewing engine, so you can preview the recovered files before saving them back to your local or remote storage.
Important Note: Don’t save the recovered files on the same drive where they were previously saved - from where they got lost.
Why Choose DiskInternals RAID Recovery?
Yeah, there are pretty many RAID Recovery tools out there, but DiskInternals RAID Recovery is much-advanced and backed by IT experts. It works very fast too, and there are three recovery modes you can choose from. Hereunder are other reasons to choose this recovery software:
- Retrieves lost files from software and hardware RAIDs
- Supports manual and automated recovery (Recovery Wizard) options
- Can save recover files from remote directories or local drive
- Supports Unicode filenames and multi-level folders
- Allows you to create backups for free (disk images)
- Automatically fixes pool and filesystem parameters, including disk order
- Recovers previous versions of files if available
- Verifies checksums to validate data credibility.
RAID Failure Prevention Tips
To prevent RAID array failure, there are some handy tips you need to know. It's simply knowing the common reasons why RAID arrays fail and then implementing safety measures that would curb those "reasons."
- Firstly, you should always monitor the RAID disk drives’ critical SMART parameters, health status, and temperature routinely. This will help you identify RAID array failure signs earlier and fix them before it escalates.
- Secondly, always back up your data regularly because no one can be too sure when data loss could occur.
- Don’t perform CHKDSK or SFC scans in a bid to fix and repair RAID array errors.
- Don’t ever use the “beta” version of a RAID firmware, OS, or system file. However, ensure to keep your OS and critical software apps updated to their latest stable versions regularly.
- Retain at least two new or empty drives, which would be used to replace failed drives in the array.
